There are two basic types of cryptographic algorithm: symmetric and asymmetric, and choosing the right type of algorithm is an important decision in IoT system design. Symmetric algorithms use the same key to both encrypt and decrypt the data, and require less processing overhead. Some of the most popular encryption algorithms, such as AES, which is very popular because it has never been reported as being hacked, use symmetric encryption. Although the algorithm is strong, the use of one secret key is a potential vulnerability, as it can be difficult to distribute and protect. Typically, symmetric encryption might use a key from 128 to 256 bits long.
Asymmetric encryption uses a “one-way” approach, with a pair of keys. A private key is kept secret and not distributed, while a public key can be shared widely. If the public key is used to encrypt, the private key is needed to decode, and vice-versa when the private key encrypts. This approach makes the system easier to manage and much more scalable. Furthermore, keys of up to 4096 bits can be used. The WaRP7 processor for example, includes support for these long, secure keys.
One requirement for encryption algorithms is the random number generator (RNG). This is used to generate the keys, which must be random to prevent a hacker from predicting the numbers and breaking the cypher. The CAAM offers National Institute of Standards and Technology (NIST) certified pseudo and true random number generators.
By providing hardware support on-chip, IoT devices can be developed that ensure a greater level of security by using stronger encryption without dramatically impacting on the processor’s capacity to run the application.
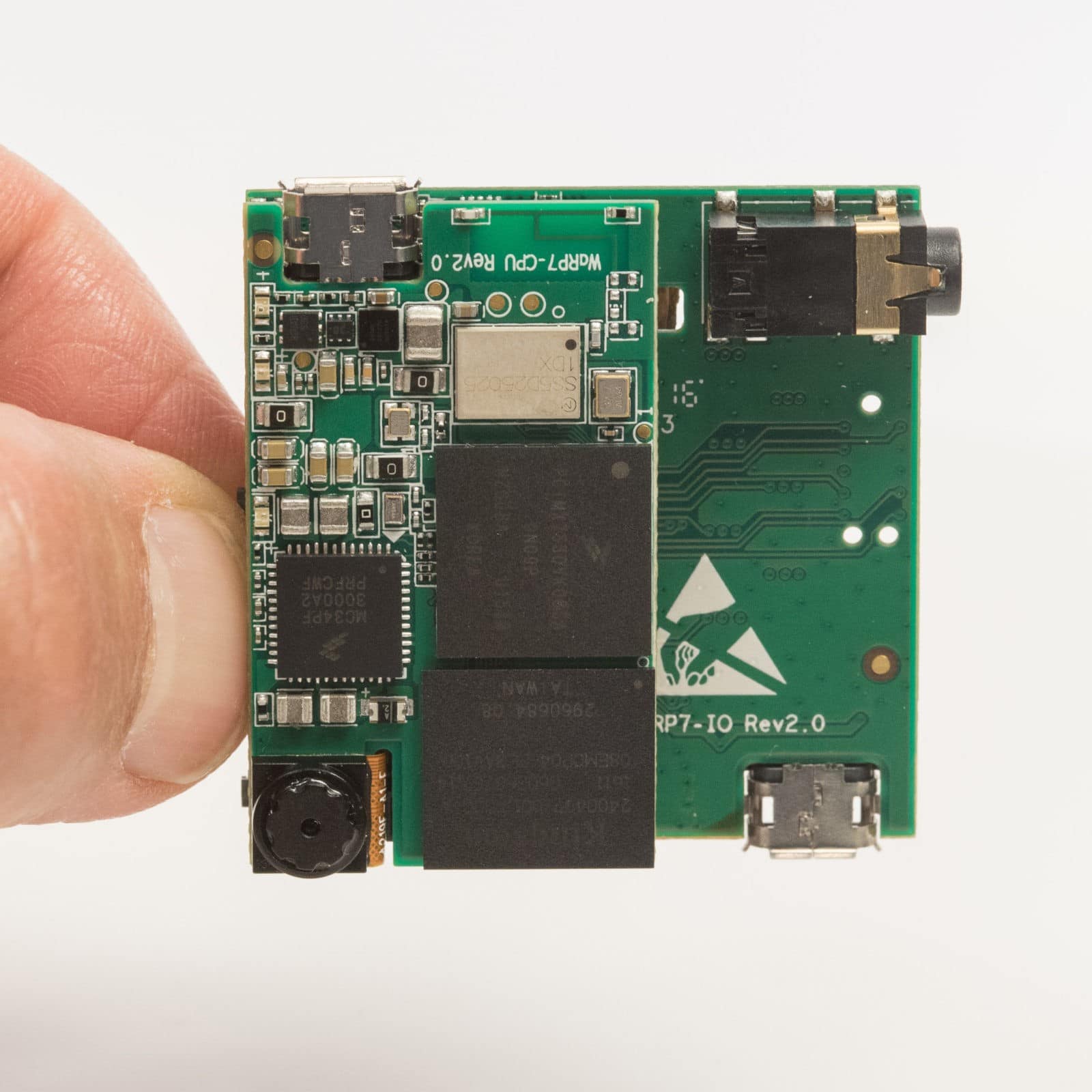
Despite the security of the algorithms available, it’s possible to use attacks that measure device power consumption to determine secret keys. This can be much easier than it sounds, as the cryptographic algorithms can involve rotating registers that contain the keys. The processor used on the WaRP7 board, however, includes countermeasures to prevent detection of keys by using simple (SPA) or differential power analysis (DPA).
IoT security is also enhanced by other features that are included on the processor used in the WaRP7, as well as some other processors. Secure non-volatile storage (SNVS) is hardware that determines whether the device is in a secure state, which in turn determines whether its resources can be accessed. When in a secure state, special cryptographic keys can be used to decrypt long-term secrets, such as public/private keypairs, DRM keys or proprietary software.
A security violation can be trigged by JTAG events, power glitches, Master Key ECC check failure, software-reported issues and hardware reported tampering using the tamper pins. When such as violation is identified, the system activates security-related hardware or software. In the case of highly sensitive applications, the tamper detect pins could trigger the hardware that will automatically and immediately erase the Zeroizable Master Key, denying access to and erasing the contents of the secure memory.
For some applications, real time clocks are a potential vulnerability. A simple example is electricity metering, where the clock could always be set to a time where the lowest rate is in force. Protecting the real-time counter using the same SNVS offers additional protection. With the WaRP7 board, engineers also have access to a monotonic counter, which cannot be reversed, protecting against “roll-back” attacks.
To ensure code integrity, processor vendors have introduced several approaches to isolate applications and ensure that the firmware of the system has not been compromised. The iMX 7Solo used in the WaRP7 includes two ARM cores that have TrustZone technology: ARM’s approach to identifying secure and non-secure worlds, blocking non-secure software from accessing secure resources directly. Effectively each physical processor has two virtual cores: one considered secure and the other non-secure.
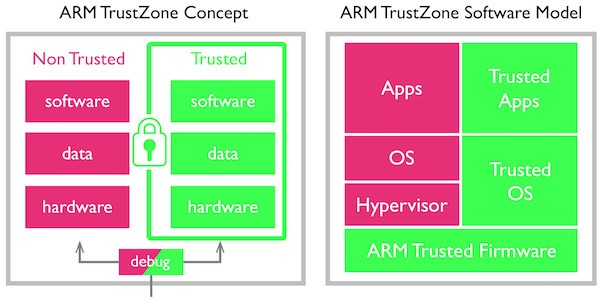
The TrustZone technology relies on secure low-level firmware. The inclusion of a high-assurance boot (HAB) feature, which uses digital signatures to recognise authentic software and prevent unauthorized software from gaining control of the boot sequence, ensures that this firmware cannot be compromised.
Dealing with the Complexity
This article has considered just one IoT board as an example of the features available to increase security. The challenge faced by engineers is the complexity that this introduces: the data sheet for the i.MX 7Solo family is 150 pages, and the reference manual runs to more than 4000 pages. Clearly help is needed to ensure that the time to learn about the features is not unrealistic.
Picking the right development platform in the first place is critical. Resources such as the element14 community’s Design Center provide detailed information about processors, development platforms, software tools and middleware. With applications engineers, also on-hand, distributors play a vital role in ensuring that the right selections are made, as well as reducing the learning curve with the appropriate tools and information.