• Or it is because of the rise of M2M (Machine to Machine Communication). IOT devices are getting ubiquitously connected. 50 billion devices connected by 2020 as per Gartner. Devices are talking to each other without human intervention even and are able to take so-called smart data-driven decision themselves. Gone are the days when you would use an app on your phone to order milk from a grocery store. Smart refrigerators can automate this. It can sense the unavailability of milk & order by itself. So is M2M & Connectivity making things smart. Actually, it’s the combination of all three. These are the three things which is making everything smart viz. Sensors, Cloud and M2M. Let it be the Wearables, the Implantables, the Injectables, the Injestibles; every smart thing is leveraging these three technologies. And if we give a closer look, all smart things are doing this.
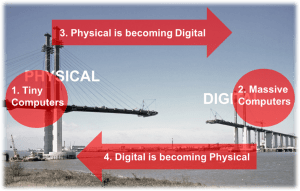
They are enabling us to bridge the gap between the physical world where we all live in and the digital world where we get the power of data-driven decisions. The tiny computers of physical world, the sensors are getting connected to the massive computers that exist in the digital world, the Cloud. They are getting connected in ways that allows the physical to become digital, to sample the world, to turn it into something that those massive big computers can ingest. And then in return we are able to take the digital and make it physical.
But, when digital things become physical, digital threats also become physical threats
• Consider the Smart Car – Jeep Cherokee by Chrysler. An awesome SUV with smart features like hands-free voice command control for dashboard functions, smart infotainment system with capabilities of integration with your iCloud & Google drive.

A pretty nice car with lot of cool smart features, but it was hacked. The hack was demonstrated in BlackHat Conference last year. The hackers Reverse Engineered the car firmware & communications protocol and took control over Dashboard functions, Steering, Transmission and Brakes. They Remotely controlled the car & showed how they can crash the car without the knowledge of the driver. Chrysler recalled 1.4 Million vehicles for the Bug fix. Imagine the loss, both in terms of money & brand-reputation.















This site is really cool. I have bookmarked it. Do you allow guest posting on your
site ? I can write hi quality posts for you. Let me know.
Please let us know what interests you and what you write on. Happy to assist.