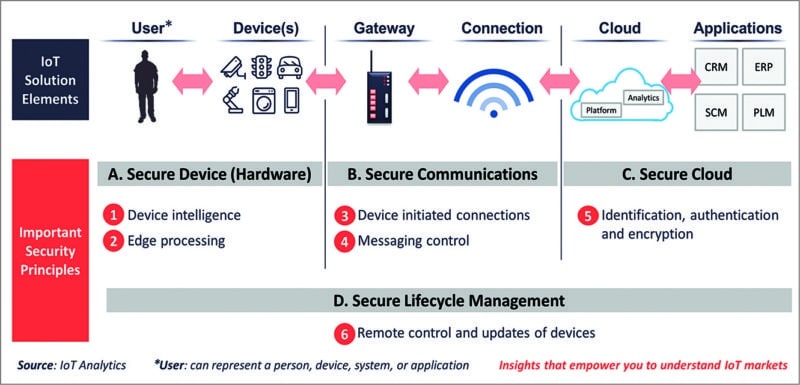
Major layers of IoT architecture
An IoT system consists of a complex multi-tiered architecture, with connectivity and security at the fulcrum of the setup. It includes the following significant layers:
Edge device and components layer
This layer consists of components like sensors, actuators and controllers embedded in or connected to the devices present in the field or at the edge. In this layer, the data is actually generated, evaluated and digitised.
Network or transport layer
Data digitised in the edge layer is transferred to the central cloud server through gateways. Connected application devices can access the data from the cloud. The cloud provides a Platform as a Service (PaaS), where the data is stored and analysed.
End application layer
This tier constitutes the operational application on the user device (smartphone, computer, smartwatch, etc). It displays and represents data captured by the sensors and shares over the cloud.
Standards to ensure IoT security
Dr Rishi Mohan Bhatnagar, president, Aeris India, and chairperson of The Institution of Engineering and Technology – IoT panel for India, said, “When it comes to IoT security, three aspects need attention-sensors, network and applications. With billions of devices coming online, we now have that many more vulnerabilities created, even if we ignore the permutations and combinations. To address the challenge, we need to have a well-etched IoT security policy and framework crafted and deployed. We also need to ensure that these policies are adhered to at all times.”
The IoT is adopting newer protocols like Message Queuing Telemetry Transport (MQTT) and Constrained Application Protocol (CoAP) due to their specific advantages. Peter Carbone, vice president and general manager of Synergy IoT Platform Business Division, Renesas Electronics Corporation, explained, “For transport, TCP/IP network software protocols are the standard. But the challenge is to support them in constrained IoT devices that are typically MCU-based as they get closer to the edge where power, cost and space are limited. A number of newer connectivity protocols have been developed over recent years that target these constrained devices. One of these protocols is MQTT using TCP with a publish-subscribe messaging pattern to reduce the volume of network traffic, improve power efficiency and decouple data exchange timing of connected objects on the network.” However, these standards need to be coupled with security protocols for effective safety. Expressing his concern, Sharma said, “The 802.11 Wi-Fi protocol has shown to be susceptible to denial-of-service (DoS) and man-in-the-middle (MiM) attacks as well as to cracking of the secret key.” Talking about the standards of data encryption systems, Hemnani said, “Today’s strong encryption and authentication schemes are based on cryptographic suites such as Advanced Encryption Suite (AES) for confidential data transport, Rivest-Shamir-Adleman for digital signatures and key transport, and Diffie-Hellman for key negotiations and management.” Transport Layer Security (TLS) standard is widely used for data-transport-level security.
Latest security measures
IoT security majorly revolves around data generated in the system and its circulation within the system. End application layer, transportation layer and field devices with embedded components play a big role in IoT security as most data transactions happen in these regions. IoT data security is largely managed with the help of cryptography algorithms, digital signatures and security certificates.
Security in transport and connectivity layer
In legacy IoT systems, Hypertext Transfer Protocol (HTTP) with secure encryption has been the common safety standard. However, it is data-intensive and comparatively slow. To mitigate these drawbacks, MQTT has become the more preferred IoT protocol layered above the transport tier. It is simple and fast with low code-footprint. These characteristics make it more suited for remote location connection or low-bandwidth actions. MQTT comes with its own set of security measures. However, these measures still leave the network vulnerable. So the trend in securing the transport layer is to secure the MQTT protocol with Secure Socket Level (SSL) certification. The most advanced version, SSL 3.0 certificate, is applied at the cloud server side as well as the mobile and devices side, encrypting communication within the network. A newer option for network security is the Transport Layer Security (TLS) 1.2 certificate. TLS, successor to SSL, has quickly picked up prominence with certain advantages over SSL, such as like better compatibility with newer browsers. Carbone shared, “For secure operation, IoT devices must protect data (and code) at rest on them, as well as data in motion. The TLS cryptographic protocol is widely used to secure data in motion by three ways: by establishing secret keys between the client and server, applying hashing algorithms to detect alteration or forgery of packet content, and establishing remote host identity using digital certificates.” For example, The Synergy IOT Software Package v.3.1.0 of Renesas Energy Corporation integrates with Express Logic’s NetX Security suite that incorporates TLS protocol for socket-layer security.
Securing the data itself
Data stored over the server is encrypted using AES security. The 128-bit AES is a strong data-encoding standard. Established by the National Institute of Standards and Technology, it works on the substitution-permutation algorithm of splitting the data in a block size of 128 bits and encrypting it with a 128-bit key length. Major businesses, including banks and financial services, use 128-bit AES data encryption.












