What if my fridge gets hacked?
May be nothing. May be the hacker gets to know how many eggs you have, or how much milk you drink. Or simply gets to know that you are not at home. But, what if one day the CBI comes knocking at your door telling that your fridge is being used for sending threatening emails to the Prime Minister of India. The attackers can easily exploit the embedded Linux in a smart refrigerator to turn it into a bot and initiate Denial of Service (DOS) Attacks on other networks.
Now why is all this happening?
Can’t we make these smart devices smart enough to be secure. What is stopping us to make IOT Secure.
IOT Landscape
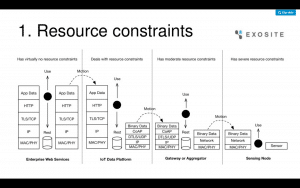
Any typical IOT deployment would look like this. Sensors in field, Aggregators & Gateways in premise, the IOT data platform which can be both in-premise or in Cloud and finally the Analytics platform in Cloud.
But as we move from the Cloud to the Fog to the Field, the biggest security challenge is the Resource Constraints problem, i.e. limited CPU, limited memory in KBs, limited power, etc. Because of that, implementing Cryptographic encryption, Digital Signatures, Anti-Virus on field devices etc. is a big challenge. Implementing a light encryption scheme on a pacemaker could decrease its battery life from about a decade to as little as a few years because the device is not designed to sustain those operations. The more resource intensive the encryption, the direr the situation.
Secondly, IOT Attack Surface is rapidly expanding. Attacks are getting innovative day by day, and they can be classified among these 6 buckets viz. STRIDE Threat Vectors.
STRIDE Threat Vectors of IOT
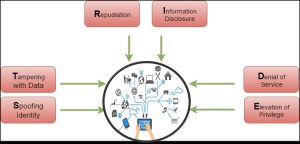
- Spoofing Identity: How can we know we are talking to the right device? Can we have lightweight PKI?
- Tampering: How to ensure data is not tampered before it is sent to the aggregator or the cloud? How can we know the IOT device is not re-calibrated by replacing its firmware?
- Repudiation: No logs are stored in field devices because of resource constraints. How can we verify later if something malicious is done from a smart field device? What about Digital Forensics in IOT?
- Information Disclosure: Field devices generally send data through radio waves without encryption. Who knows who else is collecting that data.
- Denial of Service (DOS): What if your smart car gives a message when you start it for going somewhere, “Don’t drive for next 45 minutes. Please install the critical firmware update first”.
- Elevation of Privilege: – Compromised Smart home devices have been attacked & exploited to penetrate into home Wi-Fi network to sniff regular internet traffic.













This site is really cool. I have bookmarked it. Do you allow guest posting on your
site ? I can write hi quality posts for you. Let me know.
Please let us know what interests you and what you write on. Happy to assist.