Although the Internet of Things (IoT) is one of today’s hot marketing buzzwords, most engineers have long known that there are significant benefits in adding connectivity to almost any electronic device. IoT is therefore a very broad term, covering a huge range of applications, from moving security cameras from CCTV to IP connectivity and connecting sensors in factories to wearable fitness trackers and remote control of the heating for your home.
One challenge that faces all developers of internet-connected devices is security. Why is security such a concern for IoT? The unprecedented volume of data that is available, the level of interconnectivity between all IoT systems and the potential for harm drive much of the perception of risk. One factor that should not be underestimated is the proportion of engineers who previously developed systems that were not connected to the internet who now must develop connected products.
Fortunately, suppliers, from semiconductor companies to distributors, are providing the technology and support that will enable the development of more secure IoT products, provided that engineers take the time to follow some basic principles.
Risks and Threats
The security risks associated with IoT are obvious when one considers the impact of failure of some of the systems that are connected to the internet. While major infrastructure and other safety-critical systems will have experts considering how to secure the systems and large security budgets, even something as simple and cost-sensitive as home heating systems must be secured.
At a recent meeting in Chicago, Roman Budek of NXP asserted that there are six primary security risks that designers of IoT systems must consider and address. Where data or control of the system is in the cloud, remote attacks on a cloud service providers must be considered: it is not sufficient to assume that choosing a major service provider will address this threat.
The nature of IoT means devices are often accessible, and physical attacks on peripheral systems, for example using a side channel to control a door lock, are a risk for many systems. Equally a vulnerable, counterfeit or compromised device could undermine the security of a network from the inside. This is a particular challenge as many IoT vendors believe that interoperability with other company’s products is important to ensure commercial success.
The gateway or IP edge node presents an opportunity for remote attacks. In the case of home automation, frequently the gateway is a low-cost router supplied by the customer’s ISP, which may have limited functionality and could have unpatched vulnerabilities.
Smart phones, tablets and watches present a risk as users might be persuaded to download a rogue app that would then have access to the network. Alternatively, PIN code phishing could give access to a device that has an app with access to the IoT system. Finally, as IoT matures and devices are replaced with newer products, decommissioned devices could be used as Trojan horses to compromise other network devices.
It’s clear that when designing IoT devices, engineers must take a holistic view of the whole system, and not just focus on the product they are designing.
Ensuring Security of Embedded Devices
When developing an embedded IoT device, engineers must ensure three things are achieved:
• Data Integrity: ensuring that data is protected from snooping and is only accessed by people authorised to do so, as well as making sure that the data cannot be changed to introduce either malicious or accidental errors.
• Code Integrity: securing the code is also critical. Changes to code must be detected, and only authorised changes allowed. Additionally, most companies are also concerned about protection of their intellectual property, requiring measures to prevent theft of the code
• Device integrity: it’s important to ensure that connected devices are authentic and their critical functionality has not been tampered with. IoT devices therefore need strong authentication and protection of cryptographic keys to prevent hacking and product counterfeits
To achieve this, security experts often refer to the six tenets of embedded IoT security that should underpin the approach of any developer: identity/authentication, authorization, audit, confidentiality, integrity and availability. At the heart of many of these tenets is cryptography.
Device Support for IoT Security
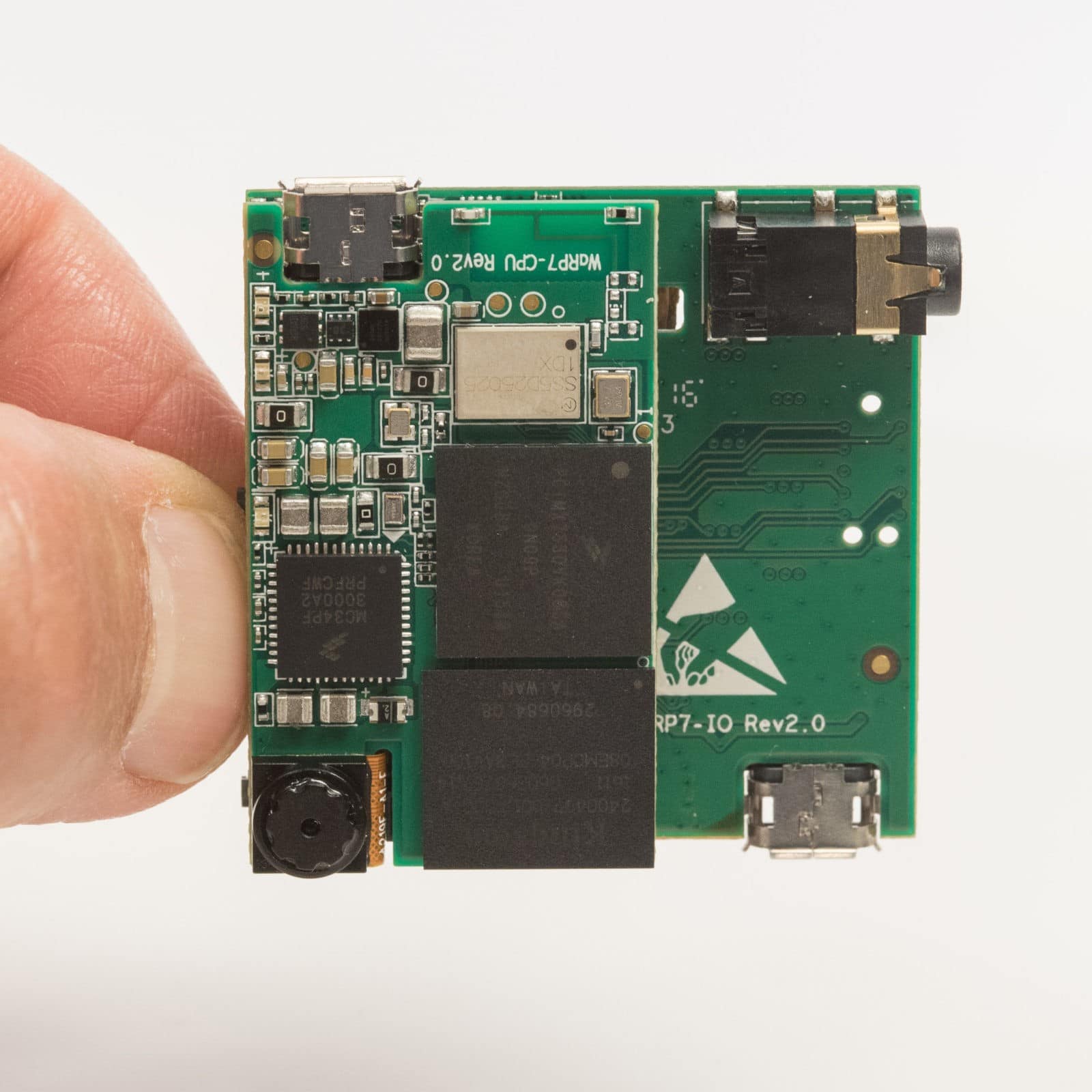
The good news for developers of IoT products is that many devices already provide support that makes it easier to build in security. Take the NXP iMX 7Solo applications processor that is used on the NXP WaRP7 IoT and Wearable Development Platform, which was developed in partnership with Premier Farnell. This IoT prototyping platform includes many security features that have been built into the processor.
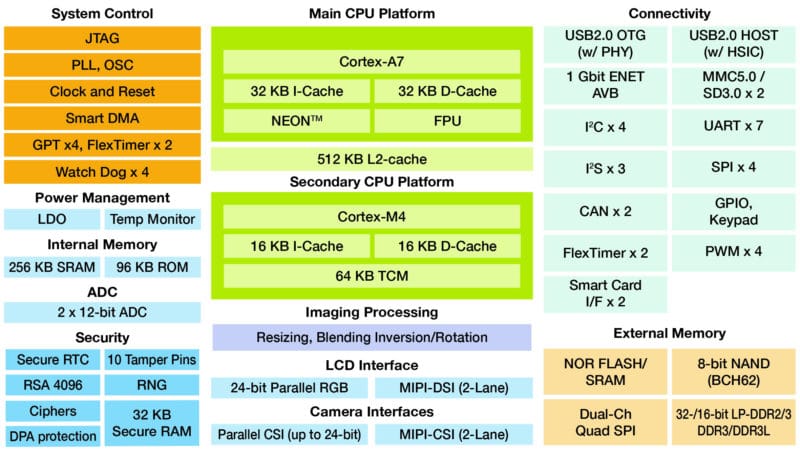
One of the most obvious features is the support for encryption. The processor also includes support for hardware-accelerated encryption with the CAAM (cryptographic acceleration and assurance module). This module contains cryptographic and hash engines that support a wide range of cryptographic standards.