The first level of analysis and interaction occurs at the edge—data is collected from a sensor (for example, a wind turbine sensor, a motor encoder or a vibration signature). This is processed locally to help understand how to tweak parameters that would give the highest efficiency or provide an early indicator of a potential failure.
The next level of analysis is done at the control room or plant level where sensor data from multiple end devices and even multiple assembly lines is aggregated to make decisions that would increase the efficiency of the factory or a process; for example, a control room making idling or sleep decisions of various end devices to reduce the overall power profile of the process.
The first two aspects of using data to positively impact operations is what you are familiar with and use in some way, shape or form. However, what the IIoT envisions is not just an increase in data collection and analysis at the first two stages, but integrating process data with enterprise data to make really interesting decisions that so far have not been made before.
Consider a company enjoying a market explosion. The assembly line can be programmed to manufacture higher volumes of the product, or completely bypass sub-assemblies adding features not valued by the market. Now, combine both the operating and financial data to provide more insight to the chief financial officer. The agility of the company and its ability to pivot, change and continue to grow can be exponential. Indeed, it is an attractive proposition, and many are eager to move forward, quickly. So quickly that security has not been keeping up with the new IIoT systems.
The IIoT exposes system vulnerabilities
There are a few ways that IIoT systems are vulnerable to attacks. Among the two most prominent are Cloud storage and network architecture.
Putting data on the Cloud (public or private) is an integral component of the IIoT. But this comes with huge security implications. Traditionally, industrial control system (ICS) vendors have maintained that their systems have a built-in air gap. This is no longer true when these systems have a direct or indirect connection to the Internet. The IIoT is going to drive the understanding that ICSes need to have embedded authentication and security features.
Let us now look at the network architecture that enables the IIoT. Fig. 3 provides a top-level view of how field devices in a factory or a manufacturing process are ultimately connected to the network.
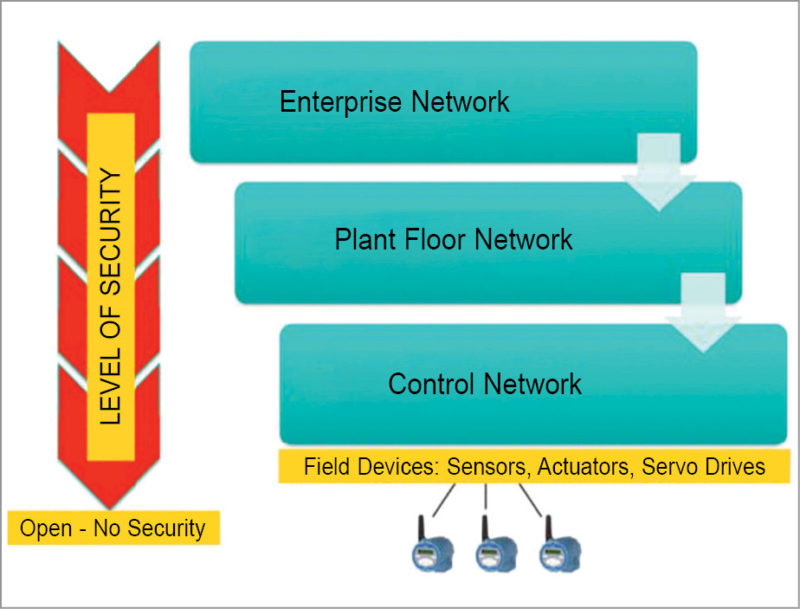
There has always been a control network, a host of field sensors, actuators or servo drives (and other such devices) connected to PLCs or distributed control systems. Typically, this control network is a bunch of isolated networks. But increasingly, control networks that manage different sections of a factory or process are connected together, creating the plant network.
A plant network lets supervisors see the entire plant operation and deduce how the different sections of a plant interact with each other. Information at this level allows for optimisation of the entire plant or an oil field. Ultimately, this plant network information is integrated with the enterprise/business network to enable the real promise of the IIoT.
Each level of operation within the control network needs to have its security needs assessed—security is different at each level. If you start at the top, the domain of IT, you have secure switches and servers that are (hopefully) updated with the latest software and patches as explained below.
• At the plant level, security is not up to date. However, IT still has some control.
• At the control network layer, PLC architectures are decades old. Generally, updates are rare, and frequent patches cannot be applied to systems that are responsible for 100 per cent factory uptime. Security is generally weak here.
• At the field level, which is generally never discussed, security is virtually nonexistent. Field devices are open, trusted and cannot really have any encryption implemented because interoperability is paramount. If you look at field slave devices, such as sensors and actuators, these systems have zero security features (for the most part) and work on protocols developed almost 30 years ago during the 1970s through the 1990s.
Addressing risks in ICSes at the field level
When you look at the field level in more depth, two primary points that present risk to the ICS are remote field sensors and I/O modules. At stake are uptime, predictable maintenance and overall industry efficiency—the cornerstones of the IIoT.
Risks with remote field sensors.
Physical security of all sensors may not always be possible, especially when the sensors are very remote like those used to monitor oil and natural gas fields. Inaccessibility further makes these vulnerable to physical attacks, so it is essential to authenticate all sensors before their data is accepted. However, in most cases, field sensors, even those used in critical infrastructure systems, are both open and trusted. This vulnerability of the field sensors has not gone unnoticed.











