The challenge with NB-IoT is that it does not fit in with LTE, hence, it calls for a separate side band with a different software setup, which could again increase deployment costs.
Lesser-known connectivity options.
Sigfox is a viable alternative to LoRa, working in the same spectrum using binary phase-shift keying (BPSK). Even though it is bidirectional, communication via Sigfox tends to be better for uplink as compared to downlink. Downlink capacity is constrained due to limitations on receiving sensitivity at endpoint. This could well work for M2M communication, where we are concerned with the status of machines and status updates happen automatically.
Availability of Sigfox modules is not an issue anymore, as Sigfox is readily selling the endpoint technology to manufacturers. Availability of endpoints makes Sigfox extremely affordable. However, cost of a base station is high, making the system at par with LoRa network.
Thread is another technology that is being talked about. It targets to change the spotty and power-hungry nature of established connections. The mesh network created in a Thread connection looks to connect hundreds of devices around your home with minimum of batteries.
As per threadgroup.org, a simple AA battery could last for years. Aggarwal explains, “It spreads on the guarantee of an IP based work organising arrangement that is secure, solid, versatile and streamlined for low-power operation.” Scalability of the network of up to 250+ devices and AES encryption to plug leaks in wireless connections add to the charm.
Weightless is a proposed wireless technology standard for exchanging data between a base station and thousands of machines around it using white space with high levels of security. White space refers to unused broadcasting frequencies in the wireless spectrum. This may not sound like much, but it becomes an important factor when you consider the capability to cover tens of kilometres in a single wireless hop. However, more realistic expectations from the system can be made after some solutions come to light.
Hardware and the open source community.
There has been a lot of focus around the IoT with regards to open source hardware in the recent past. “The open source IoT framework allows you to utilise open-sourced implements to customise an IoT platform to suit your requirements,” says Aggarwal. It provides a positive push for the initial start of product development.
Anand says, “However, due to mixed type of resource availability, product development is often left to be a subject of concern. We have a lot of IoT solutions, some of which are working towards making open source hardware applicable in real life.”
Increasing availability
Self-contained RF-certified module solutions that allow multiple protocols like TCP, UDP and IP on chip are flooding the market from various vendors. Built-in security features in these solutions help reduce certification times and allow the addition of communication to microcontroller based products. The ease of using these solutions is also increasing. Chauhan says, “The community approach allows you to take LoRa networks in your own hands. We have had successful implementations in about 100 cities with community participation.”
Anand believes, “We need to move towards applied developments with open source hardware rather than just the hobby and fun part of it.” Open source community has been helpful in supporting product development that could be made more useful with a focus towards product deployment and adoption, as it is finally critical for true success.
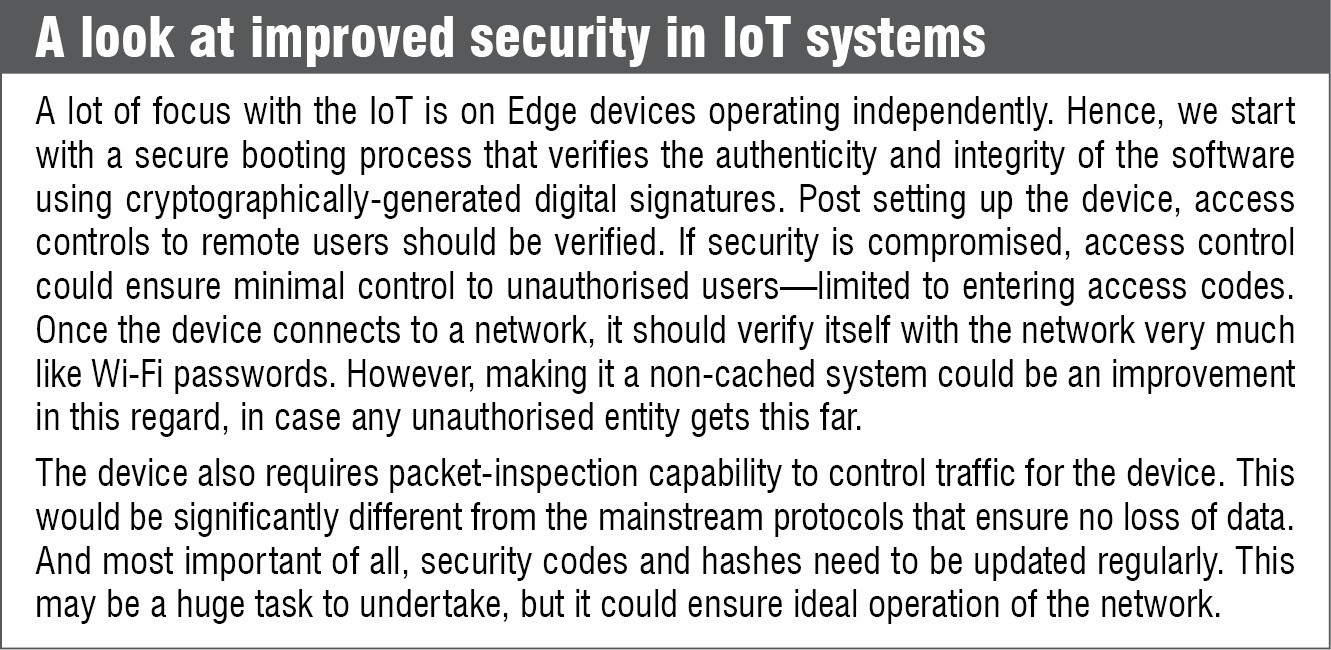
How secure are these systems
Security and analytics top the list of focus areas with IoT development. The IoT introduces a wide range of security risks and challenges to IoT devices, their platforms and operating systems, their communications and the systems to which these are connected. After all, experienced IoT security specialists are scarce, and security solutions are currently fragmented involving multiple vendors. As data volumes rise, newer analytic tools and algorithms are also needed, but as data volumes increase, traditional analytics are not enough to carry out the task.
At present, a very high number of IoT systems are open sourced and have open networks. This brings in the concern of security of these networks. These concerns are further fuelled by reports from Keeper Security, which highlight the state of passwords employed by users. Out of the one million passwords analysed by the group, a whopping 17 per cent went with the password 123456. Others in the list are no better. This brings in the question as to how secure the system can actually remain.
Improving the security.
Security technologies required to protect IoT devices and platforms from information attacks and physical tampering must be improved significantly. Encrypting the communication and addressing innovative hacks and denial-of-sleep attacks that drain batteries must be looked at for the system to last longer. Security can also be made complicated by basic processors and simple operating systems used in edge devices that do not support complex security solutions.