V.P. Sampath is an active member of IEEE and Institution of Engineers India. He is a regular contributor to national newspapers, IEEE-MAS section and has published international papers on VLSI and networks. In this article he shares his insight about FPGA and what revolves around it in the IoT zone.
Billions of devices are expected to be connected wirelessly by 2020. In this emerging era of connected devices, machines need not only be secure but also need to be secure at device, design and system levels. Internet of Things (IoT) requires diverse technology and specialised skill areas such as specialised hardware and sensor development, along with sophisticated real-time embedded firmware, cloud applications and Big Data analytics for massive real-time data into usable information, delivery of data to human-scale and human-usable platforms, particularly sophisticated smartphone apps. The IoT is revealing an important need in technology, that is, programmable hardware and I/O.
FPGA at a glance
IoT will soon be driven by field-programmable gate array (FPGA)-like devices, because these devices can interface with the outside world very easily and provide lowest power, lowest latency and best determinism. IoT would interface with temperature, pressure, position, acceleration, analogue-to-digital converters (ADCs), digital-to-analogue converters (DACs), current and voltage, among others. Arduino and Raspberry Pi could also be used
An FPGA can be considered a programmable special-purpose processor as it can handle signals at its input pins, process these and drive signals on its output pins.
The above system is very deterministic. An FPGA can interact with memory and storage devices through serialiser/deserialiser interfaces (SERDES), which also allow for Ethernet, serial or Bluetooth communication. An FPGA can, for example, take an HTTP request packet received from a wireless Ethernet component, decode its request, fetch information from memory and return the requested result back through the Ethernet device.
FPGA could be coupled with an ARM processor to leverage higher-level software functions such as Web servers or security packages, if higher level of processing is required. The key consideration is the programmable aspect of an FPGA. In a typical development cycle, a supplier development kit is employed to configure FPGA, while a printed circuit board (PCB) is developed with specific sensor/communication/display components, as required.
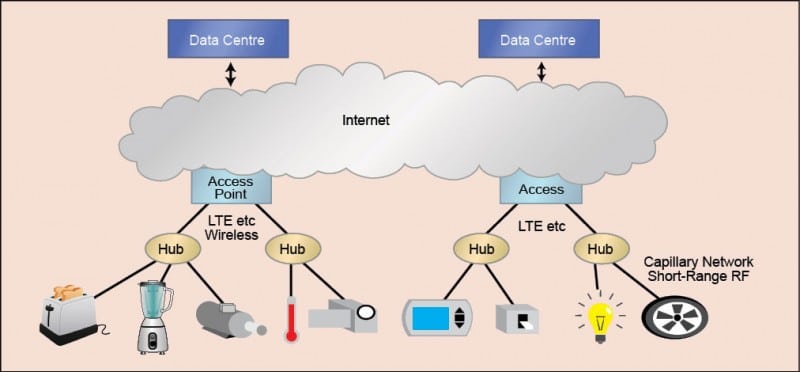 The IoT comprises at least three layers, each with its own medium and protocols
The IoT comprises at least three layers, each with its own medium and protocols
FPGA challenges
IoT challenges include security, privacy, unauthorised access, malicious control and denial of service. A hardware-first approach with respect to security and implementation of necessary functionality on the systems on chip (SoC) level is vital for fully securing devices and platforms such as FPGAs, wearables, smartphones, tablets and other intelligent appliances.
In practice, the hardware-based platform offers a single user interface (UI) across factory locations, real-time visibility into operations and remote, cloud based feature activation. IoT devices also have long life spans, yet manufacturers are likely to stop developing and rolling out patches for a product once it reaches obsolescence. For these reasons, IoT devices should leverage hardware based security and isolation mechanisms that offer robust protection against various forms of attack.
The outside layer of this network comprises physical devices that touch, or almost touch, the real world, such as sensors (optical, thermal, mechanical and others) that measure the physical states of houses, machines or people.
There are some complete control systems such as thermostats, smart appliances or drone helicopters. The presence of these complex devices introduces an encounter with the IoT in the form of sensors and actuators, or complete systems.
Consider the thermostat at home. When we add an interface to it so that a mobile app can read the temperature, check for failures and change the set-point, it works automatically. This approach wants to, whenever possible, move control onto the Internet, and ideally onto a computing cloud and scatter tiny, inexpensive sensors everywhere. Here, we eliminate the thermostat altogether and, instead, put temperature sensors around the house, inside and out. And while we are at it, we pull the controller boards out of the furnace and air-conditioner, connect their inputs and outputs to the Internet as well, so a cloud application can directly read their states and control their sub-systems.
In general, these wireless interfaces match the characteristics such as low power and the ability to sleep at very low quiescent current, long periods of sleep and short bursts of activity. But the interfaces bring with them baggage, too. These are mutually-incompatible, have a short range and use simplified, non-Internet protocol (IP) packet formats. These characteristics necessitate a new kind of device to intermediate between the capillary network and the next layer of the IoT, that is, a local IoT concentrator.
The concentrator serves as a hub for short-range radio frequency (RF) links in its immediate vicinity, manages the link interfaces and exchanges data with these. Because these concentrators are unlikely to have any direct connection to an Internet-access router, these will generally use Wi-Fi or Long Term Evolution (LTE) as a backhaul network, which then becomes the second layer of the IoT. It is the job of the hub, then, to perform routine work of a network bridge as well as packing and unpacking, shaping traffic and translating between headers used in short-range RF packets and headers necessary for backhaul networks.
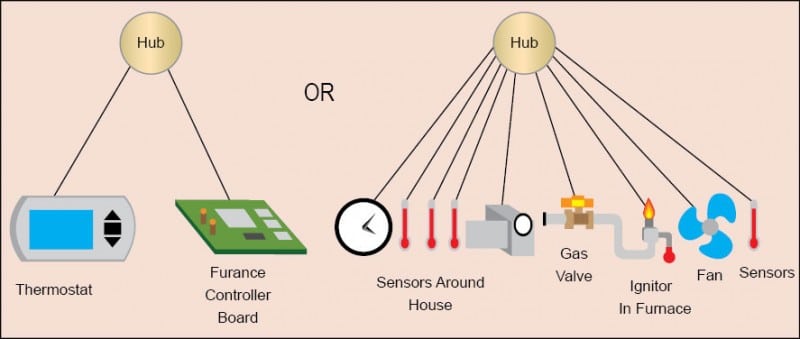 Two different concepts of IoT: connect to existing intelligent controllers (left) or connect directly to individual sensors and actuators (right) (Source: Altera)
Two different concepts of IoT: connect to existing intelligent controllers (left) or connect directly to individual sensors and actuators (right) (Source: Altera)
Future trends
In future, we can expect vehicles with an increasing amount of autonomous capabilities to navigate roads and highways, and interact with each other, their owners and the IoT. Intelligent cars and smartgrids are just the beginning of a changing ecosystem, where devices, systems and platforms that were previously disconnected will become online.
Ultimately, integration of various IoT devices and platforms will lead to the proliferation of smartcities across the globe, riding on the new digital infrastructure enabled by ubiquitous connectivity and the ever-increasing bandwidth. Thus, it is important to realise that, just because a system is embedded, it does not mean it is secure or will remain so, indefinitely.
Therefore security must be perceived as hardware rather than software patches, with chip makers routinely forced to contend with a wide range of potentially serious threats including data breaches, counterfeit components and intellectual property (IP) theft. Apart from ensuring fundamental chip security during manufacturing, embedding the right security intellectual property (IP) core into an SoC can help manufacturers design devices, platforms and systems that remain secure throughout their respective lifecycles.
Hardware-enabled examples include device provisioning, subscription management, secure payments, authorisation and return merchandise authorisation (RMA)/test support. Embedded SoC security can provide a critical root of trust, managing sensitive keys for secure boot, service authentication and key management. SoC security core can regulate debug modes to thwart reverse engineering, while providing chip authentication to prevent counterfeiting. SoC based security can also manage one-time programming of on-chip resources.
This article was first published in the August 2015 issue of Electronics For You magazine.