This article discusses threats encountered in an IoT ecosystem at different levels of connectivity and how embedded partners are enabling security.
Security in smart applications has evolved from the convergence of wireless technologies, micro-electromechanical systems (MEMS), microservices and the Internet. This concept has the potential to impact how we live and how we work. The Internet of Things (IoT) is now the focus point for all the technological advancements and research. Every product or entity that measures something or performs a specific function locally has a scope of being connected to cloud. Companies are trying to enhance their efficiency through the IoT by logging maximum data, managing the execution and analysing the data. The IoT enabling this data collection or collation plays a pivotal role. With more and more applications being considered for refinement, the amount of data proportionately gets increased.
Now imagine an entire ecosystem scoping certain points to collect data and then pushing this data to cloud, where it can be correlated and analysed to come up with more refined and defined techniques of execution. There are various points at which breach can happen, tampering the integrity of the data and its generator.
This calls for a strong security system to keep the data and entire ecosystem secured. Nodes in this ecosystem can have different methods of sharing (wired or wireless) the information. The medium essentially depends on the nature of application and product. In order to build this kind of security, one needs to identify vulnerable points in the entire system.
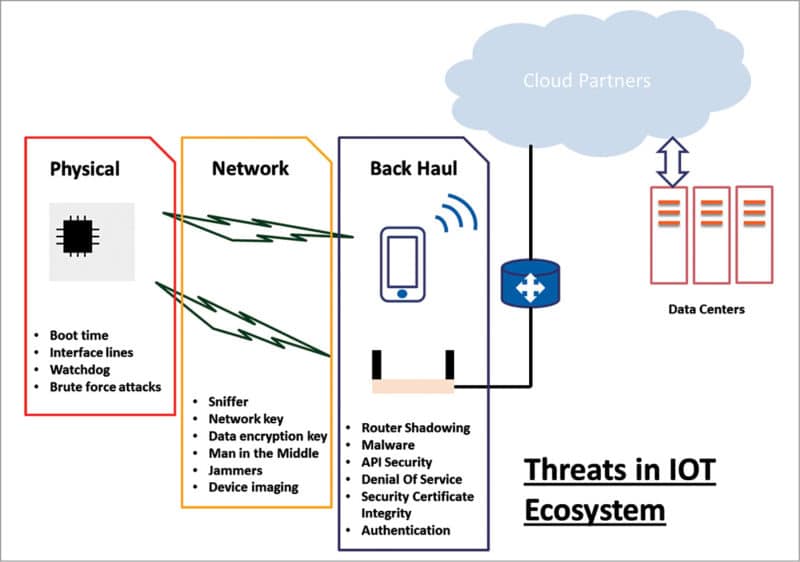
In a closed enterprise system, things were different because of limited entry and exit points for data and user access, which could be screened and validated more thoroughly. For example, you can have several firewalls for allowing an IP access to a shared folder in your local network system. There can be a MAC filtering at the router or network switch for first-level access validation into your network, followed by a username and a password that is encrypted using a private key authenticated by a unique certificate.
But in today’s usage scenario, where networks are becoming more ad-hoc in nature and the data exchanged on these is increasingly private and sensitive (whether it is someone’s personal messages or any enterprise’s key IP details), the threats are far more serious.
This is precisely the reason why security or cybersecurity has become a primary concern globally for big technology partners.
The ownership of this fight against cyber-attacks or hacking attempts lies with embedded solution partners who design the hardware and embedded application, as well as application software companies that use these products to have their designed services extended to end users. The scope of this article is limited to discussing the threats encountered in an IoT ecosystem at different levels of connectivity and how embedded partners are enabling secured solutions.
Physical
When identifying vulnerable points, the first and foremost concern is a physical hack. The physical hack can be at the boot itself (when the device is powering up), by scoping the communication lines of configuration or image readout from the external memory.
To prevent this, processors use secure boot option to have the key or configuration parameters read, decrypted and validated using the security key present in secure boot IC externally. Many processors now also support encryption of the external flash or memory using certain certificates stored in the internal flash and programmed in the factory.
The other kind of physical hack can come from detection of the external scoping of communication lines (serial interface like SPI/I2C or UART). Some processors come with inbuilt mechanisms to detect such tampering. This helps to execute internal logging of any such attempt and erase content of the external memory to protect the data and IP.
All the processors and controllers with internal flash come with JTAG interface fuse-blow option to disable readout of the internal flash, protecting the IP and keys inside. This debug security has become an essential feature among all the semiconductor solutions. Processors and controllers, or wireless SOCs, have serial bootloaders, which are secured through factory-flashed key in addition to the state of certain GPIOs at power-up. Hardware watchdog is another method to prevent tampering or physical breach of the system.
Network
While physical attacks are local in nature and require full access to hardware, things become challenging when the connectivity and access are wireless—as the advantage of medium mandates the immunity to attacks too. Fig. 3 shows some of the most common standard wireless communication protocols. Hardware has its own and most important role to support secured networking, which then gets coupled by the architecture and design of protocols used for networking. The best part of these alliances to manage communication protocol standards is that these continuously work on improving the protocols to address not only the end application’s growing requirements but also supplementing the security part.