The IoT extends from a single constrained device to a whole range of cloud systems, all connected by a set of IoT protocols that allow devices and servers to talk to one another.
When you surf the Internet or purchase a cellphone on, say, Flipkart, you use Hyper Text Transfer Protocol Secure (HTTPS), Transmission Control Protocol (TCP), Domain Name System (DNS), IPv6 or IPv4 data link layer protocols and 802.3 protocols. These are basic networking protocols inside a browser, computer’s operating system and asymmetric digital subscriber line (ADSL) router. You use these protocols even while checking an email on your computer.
Protocols are the building blocks of all networking technologies on the Internet. These are software, and size of these protocols in Windows operating system is in megabytes.
Researchers all over the world are trying to reduce the size of TCP/IP protocols.
HTTP is a software protocol, which comes inbuilt in the Internet browser, such as Chrome. It sends commands to the Web server and gets replies from the same. This software listens on port number 80 and receives IP packet on 10.100.10.11 IP address.
Let us take an example. Flipkart uses the secure HTTPS protocol to communicate with the browser. This is a new protocol. It listens on port number 443 and 10.100.10.11 IP address. (Port number is a 16-bit logical number between 0 and 65535.) Here, IP address did not change, but port number did.
Port number and IP address form the socket. Hence, the Internet uses socket for communication. A secure socket opens between the browser and Flipkart’s Web server. DNS protocol resolves www.flipkart.com string to the IP address of Flipkart’s Web server. This IP address is fixed.
TCP protocol helps carry packets from the computer to Flipkart’s server, bit by bit without error. Ethernet 802.3 protocol provides packets at the local network on the physical layer of Flipkart’s office. Flipkart’s server must be connected to a LAN or optical network.
This infrastructure is available for understanding the communication between two computers. This is how we use the Internet or shop online on e-commerce websites such as Flipkart.
Now, let us see how we can relate the above narrative to an Internet of Things (IoT) system. Basic functions of Internet communication remain the same. An IoT system also uses HTTP protocol. This protocol uses GET/POST commands to communicate with the Web server. But instead of the browser sending commands to the server, the IoT device (hardware browser) sends commands automatically to a pre-defined IP address of the manufacturer’s server.
HTTP protocol is programmed in a tiny microcontroller (MCU). The MCU is part of the IoT sensor/device.
Similarly, other protocols are also used in the IoT ecosystem. However, focus of the IoT device is to design a constrain-oriented system. IoT devices work on wired or wireless networks, with low power and small memory footprint requirements. Hence, many new protocols are evolving for the IoT, and older ones are being adapted as per the functionalities of the IoT.
Functions of an IoT system are given below:
- Addressing constrained IoT devices/sensors
- Handling packet delivery from IoT devices to gateway, server or cloud
- Discovering devices (scanning constrained IoT devices rapidly)
- Handling packets, segments or datagrams on heterogeneous multifunctional networks
- Routing network layer packets
- Securing tampering, spoofing and eavesdropping IoT data
- Updating IoT firmware
These functions suggest a requirement for new protocols for running the IoT ecosystem.
IPv4 cannot address billions of IoT devices already in play, since it uses 32-bit addresses. Moreover, a large number of IP addresses are already using IPv4.
IPv6 has the capability of handling 128-bit addresses. This protocol supports 2128 addresses more easily.
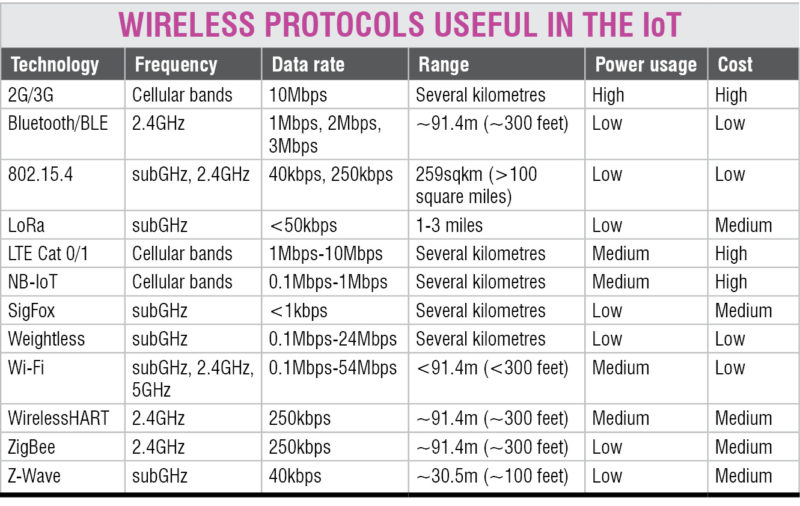
Now, there are suggestions for using 6LoWPAN IPv6-based low-power wireless personal area network protocol. This protocol uses 802.15.4 wireless link technology. It works on 2.4GHz frequency, with a data transfer rate of 250kbps. The table above features the various protocols evolving in the IoT on wireless front.
Constrained Application Protocol (CoAP) is another application layer protocol designed for IoT systems. This protocol supports four methods, namely, GET, POST, PUT and Delete. This is a small HTTP protocol but supports encryption and multicasting. It enables communication between multiple devices at one time.
Another protocol for the IoT is Message Queuing Telemetry Transport (MQTT). It is useful for remote location connection with a small memory footprint of IoT devices.
Universal Plug-and-Play (UPnP) protocol is the most important protocol in the embedded systems industry. It was developed in C language by Dr Adam Dunkel, who also developed the code for this protocol. This works well for LPC1768 MCU. It is an open source code, which is used by more than 200 vendors for providing TCP/IP communication in their IoT devices. This protocol is most tested on platforms having multiple MCUs.
Access control is another function of the IoT ecosystem. A fine-tuned protocol or specification is needed to implement access control in IoT devices. This specification is called MUD, which stands for Manufacturer Usage Description.
How is this useful for IoT devices? According to Internet Engineering Task Force (IETF), “A light bulb is intended to light a room. It may be remotely-controlled through the network, and it may make use of a rendezvous service of some form, such as an application on a smartphone. What we can say about that light bulb, then, is that, all other network access is unwanted. It will not contact a news service, nor speak to the refrigerator, and it has no need of a printer or other devices. It has no social networking friends. Therefore an access list applied to the bulb that states that it will only connect to the single rendezvous service will not impede the light bulb in performing its function, while at the same time allowing the network to provide both it and other devices an additional layer of protection.”
In simple words, bio-data of each IoT device can be defined with this specification. By reading the bio-data of a device, other devices can understand the expected functionality of that device. This defines how a toaster will communicate with a refrigerator in a connected home.
Tularam M. Bansod is proprietor of TMB Enterprises, a startup focussed on embedded systems domain. He has authored two books on microcontroller programming